
Use what I’m about to say in this article only for the right purposes, such as raising security awareness and improving the security posture of your environments. I do not accept any responsibility for other uses.
Enum4Linux is a tool used to collect information from Windows and Samba systems. Some information that Enum4Linux can collect;
->Shared files and directories of the target system,
->Working users and groups of the target system,
->NetBIOS name and IP address of the target system,
->Operating system version of the target system,
->Security settings of the target system.
Enum4linux is a tool written in Perl language used in collecting information in penetration tests. So let’s talk about how we can use it.
Requirements
-> Kali Linux ->Metasploitable
First of all, deploy Metasploitable, a vulnerable Linux variant, to your environment. Metasploitable’s default username and password is “msfadmin“. Log in with this information.
Metasploitable does not have a graphical interface by default and I used Metasploitable in one of my previous articles, “Exploiting the Shellshock Vulnerability and Protecting Yourself against It“, where I explained another vulnerability, the Shellshock vulnerability.
Let’s see which ports are open by starting an nmap scan from our Attacker machine.
nmap -Pn <Target-IP>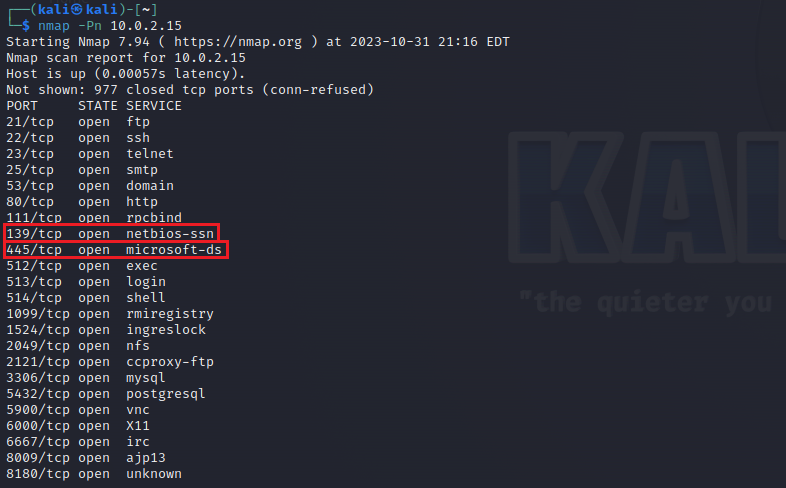
As we see, our SMB ports are open on the target machine. This means that we can continue to look for vulnerabilities in these ports with enum4linux.
The -U parameter is used to list the users on the target.
enum4linux -U <Target-IP>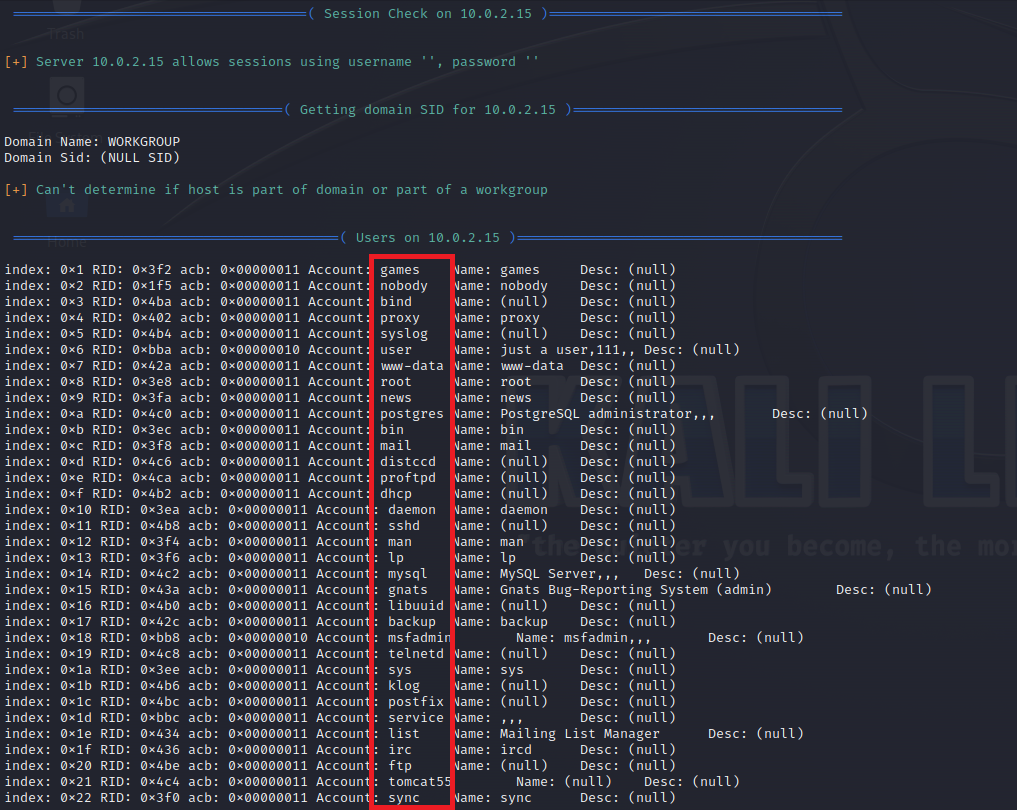
We can see the status of shared environments by using the -S parameter.
enum4linux -S <Target-IP>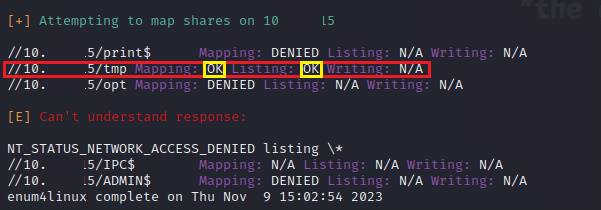
As you can see, we understand that we have access to the <Target-IP>/tmp directory and have permission to list it.
We can see the status of password policy informations by using the -P parameter.
enum4linux -P <Target-IP>
We can check the status of NetBIOS services using the -n parameter.
enum4linux -n <Target-IP>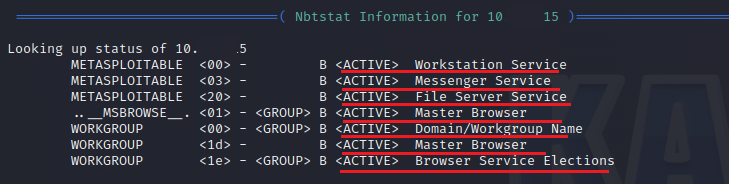
We can check the all SIDs using the -r parameter.
enum4linux -r <Target-IP>
What needs to be done to avoid such scanning and information acquisition attacks;
->Turn off unused services, ->Staying away from vulnerable protocols, ->Use strong passwords, ->Delete unnecessary users from the system,
Resources Used
-> https://null-byte.wonderhowto.com/how-to/enumerate-smb-with-enum4linux-smbclient-0198049/
Leave a Reply