
PeStudio is an analysis tool with which we can get information about executables without running them. We can do static analysis of a malware with PeStudion. Static analysis examines the contents and properties of a file, trying to gain information about what the file can do at run time. It is a type of analysis performed by examining the code and data structures of the software.
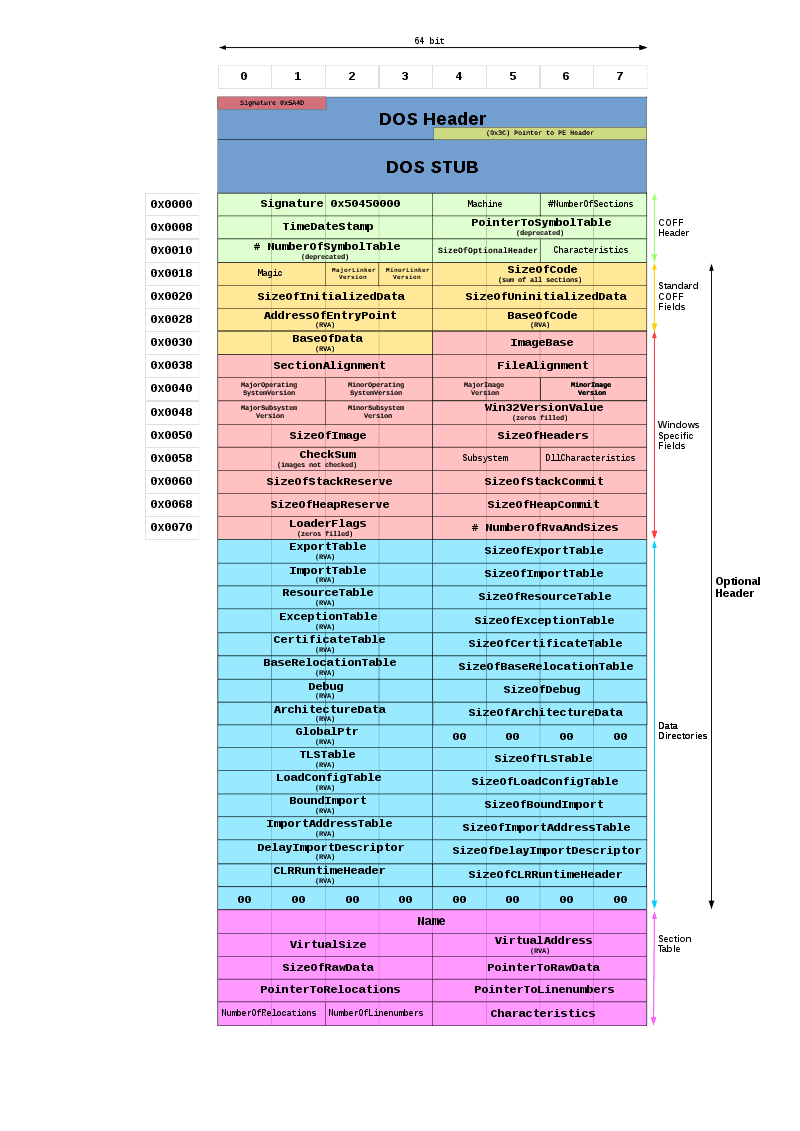
A PE basically consists of the following components, and PeStudio examines these components.
PeStudio has a structure that does not require installation. We can download it from the link below.
https://www.winitor.com/download
After downloading, we can start analysis by selecting our file.
Now, let’s do a static analysis of this malware with PeStudio using a real malware.
When we import our Executable file into PeStudio, we see directly in the general tab that the first byte of this file is 4D 5A in hex format. In text, it corresponds to MZ. This is enough for us to understand that this file is a PE.

We see that this malware was compiled using Visual Studio 2015.

Indicators
In the Indicators section, it shows us the parts that PeStudio considers suspicious as a result of its analysis on the pe. It draws attention to the points that need to be focused on for more detailed analysis.

VirusTotal
When we come to the Virustotal tab, we can see information about which security manufacturers perceive this malware as harmful or harmless.

Sections
Executables consist of sections, which are logical sections to organize the internal structure of the file, manage and optimize memory space. These sections are the code and data blocks that make up the pe file. Each section is separate and can have specific memory access permissions. Standard sections include: Some of these sections;
.text: The code section contains the program’s instructions – it is read-only. That is, it contains machine codes. Machine code is the instructions that the computer will execute.
.data: This section contains the variables and other data of the file.
.bss: This section contains the variables of the file that have not been initialized yet.
.rdata: This section contains the readable data of the file.
.edata:This section contains the exported data of the file.
.idata: This section contains the imported data of the file.

In the file-ration section, we can see which section takes up how much space in the binary. It can be said that the executable is suspicious if the area occupied by the .rdata and .data sections is larger than half of the area occupied by the .text section. Because this means the executable contains too much data or variables.
If we talk about the Raw-Size and Virtual-Size sections here, Raw-Size refers to the byte value that the section occupies in the binary, while Virutal-Size refers to the byte value of the executable after it is loaded into memory. While small byte differences are insignificant, large differences may indicate a payload, which can be an extremely suspicious situation.
Libraries
The Libraries section contains the .dll files used by this executable.

Here we see that PeStudio has marked some .dll files. These are .dll files that definitely need more attention. Coming to the reason;
WS2_32.dll: It is a .dll that contains Winsock API functions. This .dll contains the functions required for network communication using TCP/IP and other network protocols. In other words, this means that the executable may be making a request to the C2 server.
SETUPAPI.dll: This .dll file is used to install or uninstall software, update software, and manage software components. Therefore, it can go to C2 together with WS2_32.dll and download other malicious payloads, and can install these software with the functions in this .dll.
CRYPT32.dll: This .dl file is generally used for encryption and decryption purposes. In other words, the executable can encrypt the data on the host it is located on by using this .dll file.
Imports
The Import tab shows us the native APIs used by the executable used by PE.

It not only shows, but also flags for us some APIs that may cause suspicious use and shows which miter technique they correspond to.

For example, it seems that it aims to use some functions of WS2_32.dll, and it can be thought that this executable aims to initiate a connection with the C2 server and extract data.

Resources
The Resources section shows the images, icons and metadata used by PE. As seen here, the language appears to be Russian, which is a reason to suspect PE.

Strings
When we come to the Strings section, we can see the strings in ASCII format, which is in the executable and is the format that we can read.

When we pay attention to strings, we see structures that attract suspicion.
Part 1 contains many SQL queries. We see many of these queries regarding strings.
Part 2, we see that the IP address is 193.233.255.91. When we examine it in Virus Total, we see that this IP is labeled as malicious IP by 5 different security manufacturers. I think Executable sends requests to this IP address during run time.

Part 3, there is a URL where you can obtain the IP address of the host it is running on.
Part 4, we see strings containing complex letters, which is something we do not expect to be in an executable.
Overlay
When we come to the overlay section, we see that the executable does not have a signature. This increases our suspicion that the relevant executable is malicious.

As you can see, static analysis can be done in this way without running a PE using PsStudio. This gives us a broader perspective on whether PE is harmful or not.
Leave a Reply